
Cisco Vulnerability: A Potential Gateway for Hackers
A recently disclosed flaw in Cisco’s Integrated Management Controller (IMC) has raised concerns amongst businesses and individuals. Experts warn that this high-severity vulnerability could allow…
Affected Systems: Any systems using Apache Log4j2 2.0 beta9 through 2.15.0
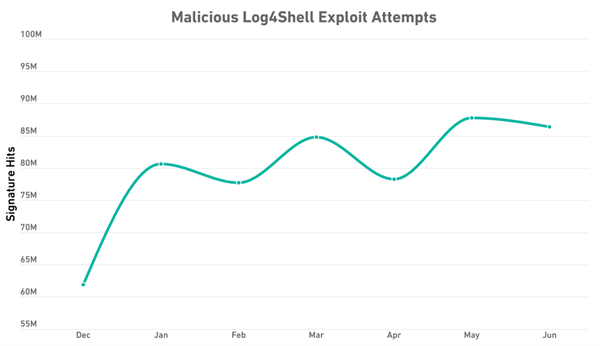
The mid-year cyber threat report published by SonicWall has detailed how SonicWall’s systems have detected over 557.5 million attempts to exploit the Log4J vulnerability between December 11th 2021 and June 30th 2022. The report also noted that there have been more exploitation attempts seen in each month of 2022 than there were seen in December 2021, when the vulnerability was first identified.
Research published by Rezilion in April 2022 found that there are over 90,000 internet facing-devices and 68,000 servers that are still vulnerable to the Log4J exploit – a number which they described as being ‘just the tip of the iceberg’, as the true number of vulnerable devices and applications may be much higher.
The high number of attempted exploits resulted in the US Cyber Safety Review Board classifying Log4J as an endemic vulnerability at the start of July, stating that there is still a significant risk of attacks using the vulnerability, and that “vulnerable instances of Log4j will remain in systems for many years to come”.
Prevention:
Installing updates immediately on applications that use Log4j should prevent the vulnerability from being exploited. If you are unsure of which applications you use may be vulnerable, the NCSC has a regularly updated list of vulnerable software, which can be found here.
Additionally, deploying protective network monitoring and blocking systems can help prevent any malicious activity from accessing vulnerable systems within your network.
The NCSC has more technical guidance available for Log4j available here.
Related Links:
https://www.cisa.gov/sites/default/files/publications/CSRB-Report-on-Log4-July-11-2022_508.pdf – Published July 11th