Affected Platforms: Microsoft 365 Authentication Process.
Date Discovered: Phishing attacks started in September 2021. Microsoft published a report detailing how the Multifactor Authentication (MFA) process is bypassed by the attacks on 12th July 2022.
“A large-scale phishing campaign that used adversary-in-the-middle (AiTM) phishing sites stole passwords, hijacked a user’s sign-in session, and skipped the authentication process even if the user had enabled multifactor authentication (MFA)”. – Microsoft
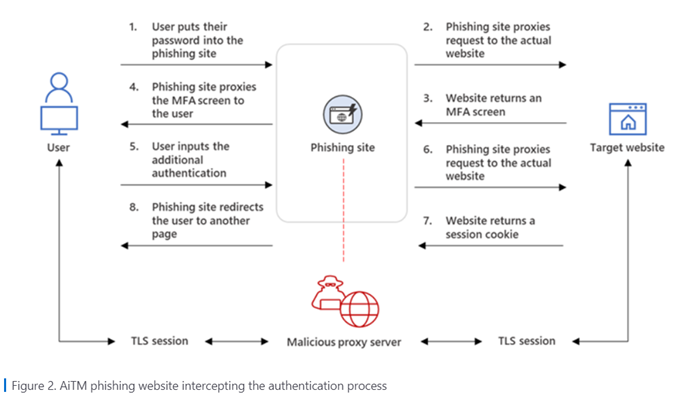
Attackers have been using fake Microsoft authentication sites to get users to share their login details. These login details are then sent to Microsoft’s website. If Microsoft requires Multifactor Authentication (MFA), the attackers are able to use the session cookies created once the victim authenticates the login to then access their accounts.
The below graphic illustrates the AiTM phishing process:
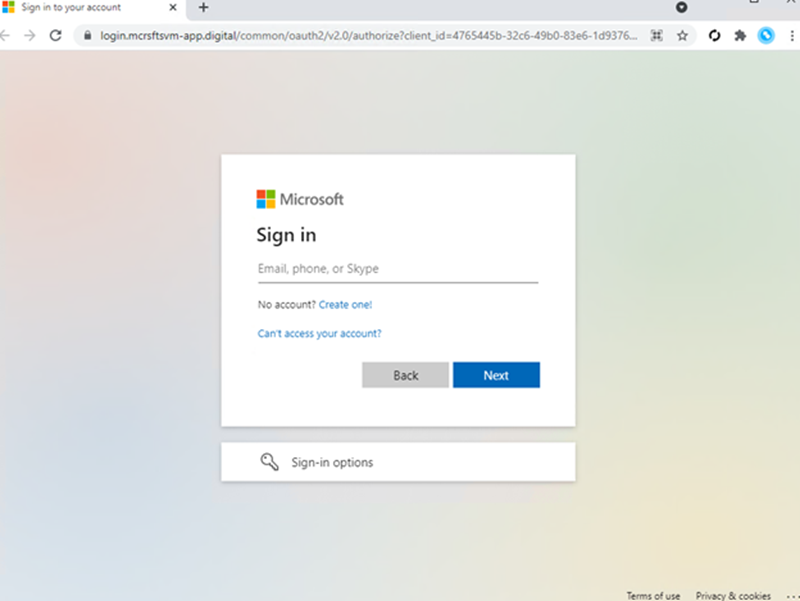
Microsoft stated that some of the phishing emails are received with HTML files attached, however, a well-crafted phishing attack would normally include a hyperlink within the email. The sample phishing landing pages shared by Microsoft in their report look legitimate and it’s easy to see why users wouldn’t suspect anything untoward.
Sample of Microsoft 365 phishing landing page:
“While AiTM phishing attempts to circumvent MFA, it’s important to underscore that MFA implementation remains an essential pillar in identity security. MFA is still very effective at stopping a wide variety of threats; its effectiveness is why AiTM phishing emerged in the first place. Organizations can thus make their MFA implementation “phish-resistant” by using solutions that support Fast ID Online (FIDO) v2.0 and certificate-based authentication.” – Microsoft
Microsoft recommends several solutions to prevent such attacks:
Be vigilant to common cyber threats:
Ensure employees are prepared for any kind of cyber incident; consider implementing cyber user awareness training to embed a culture of good practice around cyber security. Phishing is the most common type of cyber threat a business faces today, with 83% of attacks in the last 12 months stemming from successful phishing attempts (Cyber Security Breaches Survey 2022).
- If you receive a phishing email, report it to your IT team or Managed IT provider who will block the domain immediately.
- You can also report suspicious emails to the NCSC at [email protected].
Another way to mitigate against a potential phishing attack is going through a cyber-exercising scenario. Exercise in a Box, developed by the NCSC and delivered by SBRC is a free 90-minute, non-technical workshop that helps organisations find out how resilient they are to cyber attacks and practice their response in a safe environment. Find out more about Exercise in a Box here.