
Python Backdoor Utilised by Hackers in Zero-Day Attack on Palo Alto Networks
Threat actors exploited a newly disclosed zero-day flaw in Palo Alto Networks PAN-OS software. This flaw, tracked as CVE-2024-3400, is a command injection flaw that…
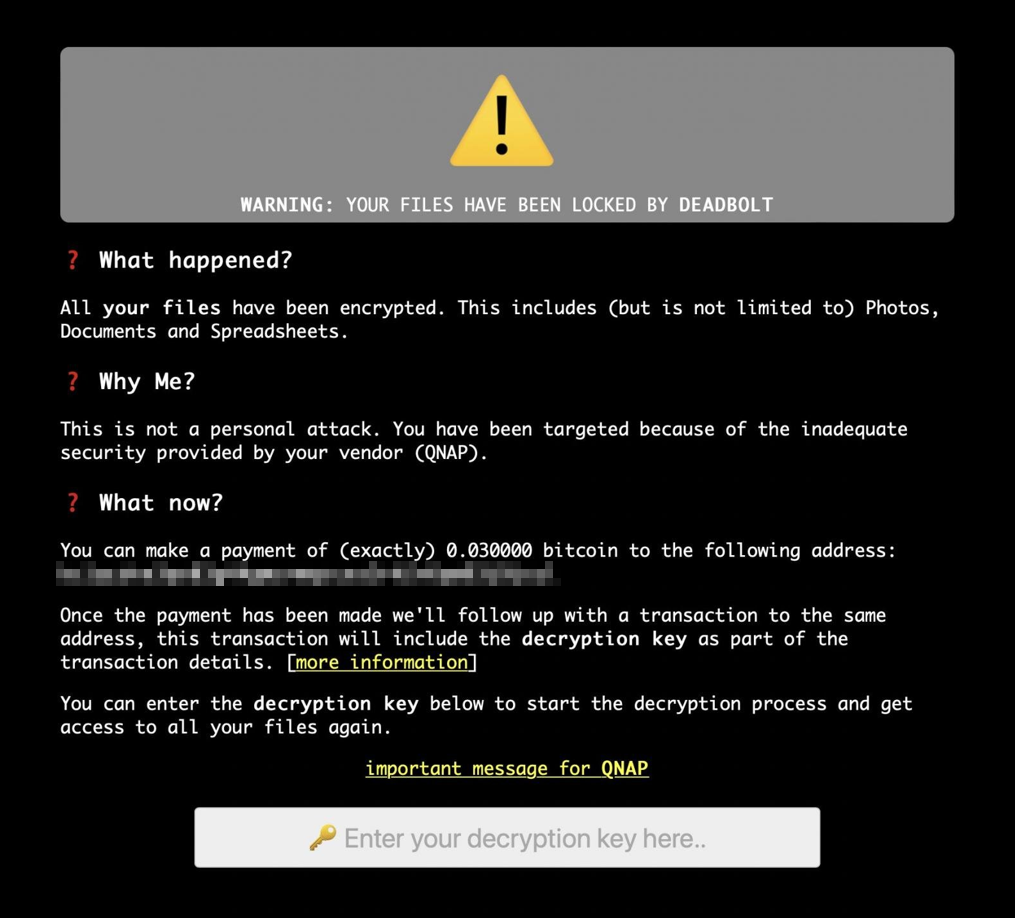
QNAP Network Attached Storage (NAS) devices are a particular product that a number of ransomware operators are currently targeting. Previous strains have included QLocker and ech0raix, the latter was infecting systems just as recently as December 2021.
The current strain that has been actively infecting systems recently is named DeadBolt. It is particularly severe given that it was reported that infections were caused through exploitation of a zero day.
These systems are unlikely to be used in enterprise environments and instead, used by small businesses, sole contractors and in some cases, personal use. Also, owners of systems may not necessarily operate within the IT sector. QNAP NAS systems are commonly exposed to the Internet via port forwarding rules configured on ISP provided equipment.
If you own a QNAP NAS system, we recommend ensuring the following actions are taken:
There are also reports that QNAP forced systems to update to 5.0.0.1891 build 20211221 even when automatic updates were disabled. However, our research has identified that there are still a substantial number of systems in Scotland running older versions, which do not appear to have benefitted from this approach.
The latest available version of firmware available is 5.0.0.1891 build 20211221 at the time of writing. However, there are reports that a user has confirmed that a DeadBolt infection occurred despite updating to this version, though it is not known whether the system was compromised prior to the update and the encryption tooling detonated later and to date, QNAP have not commented on this case specifically.
We recommend that ingress access to the system from the Internet is removed, rather than rely solely on patching. This will help prevent the system from being exploited, in the event other vulnerabilities are discovered in future.
If you have been impacted by ransomware, or require assistance, please contact 01786 437 472 for additional support. We also recommend contacting Police Scotland on 101 if impacted, even if the ransom has been paid.
QNAP Vendor Specific Guidance: