
Scottish Charity to Receive Free Year of Cyber Advance Service
We are providing one Scottish charity with the chance to benefit from our Cyber Advance service at no cost for a full year. We’re also…
An insider threat is a security risk that originates within the targeted organisation. This doesn’t mean that the actor must be a current employee or officer in the organisation. They could be a consultant, former employee, business partner, or board member.
34% of data breaches in the 2019 Verizon Data Breach Investigations Report involve internal actors.
According to the 2019 Varonis Data Risk Report, 17% of all sensitive files were accessible to every employee. In 2021, Varonis published blogs that showed this increased as high as 20% for several industries. The 2021 SAAS Risk Report goes further to highlight that 15% of employees transfer data to personal accounts and 75% of contractor identities remain active even after they leave.
So what do these statistics tell us? Insiders have the capabilities, motivations, and privileges needed to steal important data – which makes it a CISO’s job to identify and build a defence against all of those attack vectors.
Anyone who has insider knowledge and/or access to the organisation’s confidential data, IT, or network resources is a potential insider threat.
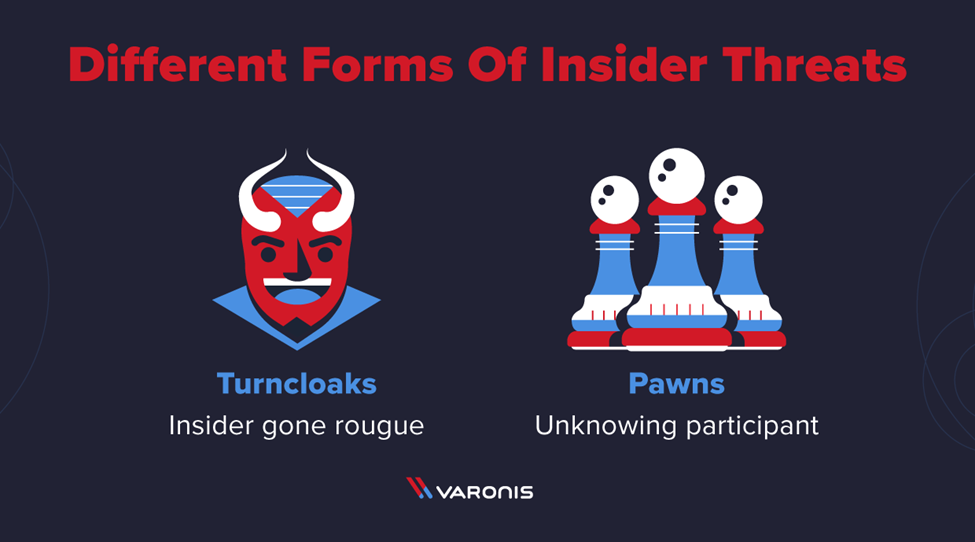
In order to protect your organisation from insider threats, it’s important to understand what insider threats look like. The two main types of insider threats are turncloaks and pawns, which are malicious insiders and unwilling participants, respectively.
A turncloak is an insider who is maliciously stealing data. In most cases, it’s an employee or contractor – someone who is supposed to be on the network and has legitimate credentials but is abusing their access for fun or profit. We’ve seen all sorts of motives that drive this type of behaviour: some as sinister as selling secrets to foreign governments, others as simple as taking a few documents to a competitor upon resignation.
Gregory Chung, an engineer at Boeing, is an infamous turncloak. Mr. Chung was convicted of using his security clearance at Boeing to smuggle trade secrets to China in exchange for a small fortune.
The LockBit and LAPSUS$ ransomware groups are well known to recruit or bribe insiders at target corporations to provide access to the network. Using the insider-provided credentials (including MFA tokens) the groups can steal and encrypt data to extort payments without going through the hard effort of getting through all the perimeter and network security defenses.
A pawn is just a normal employee – a do-gooder who makes a mistake that is exploited by a bad actor or otherwise leads to data loss or compromise. Whether it’s a lost laptop, mistakenly emailing a sensitive document to the wrong person, or executing a malicious Word macro, the pawn is an unintentional participant in a security incident.

There are common behaviours that suggest an active insider threat – whether digitally or in person. These indicators are important for CISOs, security architects, and their teams to monitor, detect, and stop potential insider threats.
See the common digital and behavioral signs of an insider threat below.
While human behavioral warnings can be an indication of potential issues, digital forensics and analytics are the most efficient ways to detect insider threats. User Behaviour Analytics (UBA) and security analytics help detect potential insider threats, analysing and alerting when a user behaves suspiciously or outside of their typical behavior.
Tesla: A malicious insider sabotaged systems and sent proprietary data to third parties.
Facebook: A security engineer abused his access to stalk women.
Coca-Cola: A malicious insider stole a hard drive full of personnel data.
Suntrust Bank: A malicious insider stole personal data, including account information, for 1.5 million customers to provide to a criminal organisation.
A data breach of 10 million records costs an organisation around $3 million – and as the adage says, “an ounce of prevention is worth a pound of cure.”
Because insiders are already inside, you can’t rely on traditional perimeter security measures to protect your company. Furthermore, since it’s an insider – who is primarily responsible for dealing with the situation? Is it IT, or HR, is it a legal issue? Or is it all three and the CISO’s team? Creating and socialising a policy to act on potential insider threats needs to come from the top of the organisation.
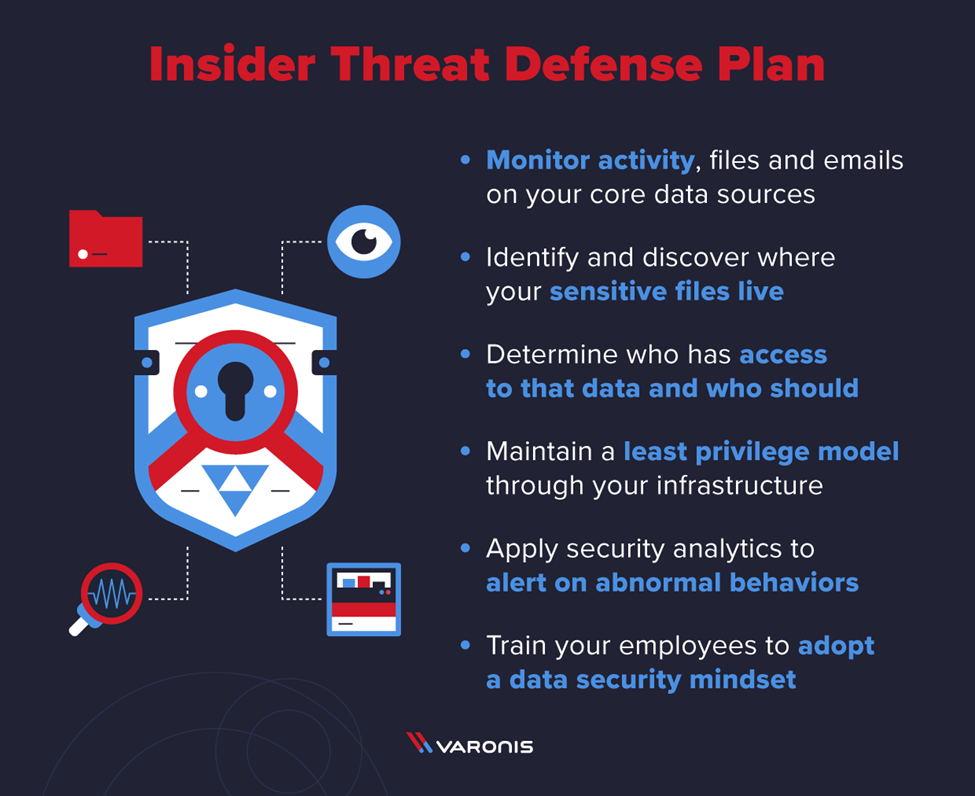
The key to account for and remediate insider threats is to have the right approach – and the right solutions in place to detect and protect against insider threats.

It’s equally important to have a response plan in place to respond to a potential data breach:
The secret to defending against insider threats is to monitor your data, gather information, and trigger alerts on abnormal behavior.
Check out the section below for questions frequently asked about insider threats.
Q: What are insider threat indicators?
A: Insider threat indicators are clues that could help you stop an insider attack before it becomes a data breach. Human behaviors are the primary indicators of potential insider threats. Train your team to recognize different abnormal behaviors and use Varonis to detect activity that indicates a potential insider threat. Like a user accessing data, they have never touched before or copying large amounts of data from one place to another.
Q: What motivates an insider threat?
A: The primary motivation for an insider attack is money. 34% of data breaches in 2019 are insider attacks. 71% of data breaches are motivated by money. 25% of breaches are motivated by espionage or attempts to gain a strategic advantage, which makes that the second motivator. The majority of insiders want to make a quick buck off the data that they stole.
Q: How do you detect an insider who is supposed to be accessing sensitive data?
A: Users need to access sensitive data as part of their job. You, the security professional, need to discern intent as those users perform their job. You can’t determine intent with a single input – you need multiple data points. Ask yourself – Does the user regularly access this data? Is the user exhibiting any other abnormal behaviours? Are they uploading large quantities of data to email? You can also use Varonis to analyze user behaviours and help you determine what is normal or not.
Q: Are threshold-based alerts prone to false positives? (e.g. simply re-structuring folders)
A: Threshold-based alerts are bad at determining intent, and can lead security pros on wild snipe hunts or a “cry warg” situation. Here is a simple scenario – a user moves one folder of sensitive data to a new location. If you have a threshold-based alert for “500 file operations on sensitive data in one minute” that user just tripped it (I won’t get into the details of why just trust me). Your security team’s time is more precious than chasing down every folder change. Use security analytics to make more intelligent alerting instead.
Q: How useful are watch lists?
A: Watch lists – lists of users that you need to keep an eye on – can be helpful, but they have a real dark side as well. If you think about watch lists hard enough, you can easily see how they could become overused and put your security team in a difficult position with the rest of your users. On the flip side, you want your users to be “security aware” and have a safe method to report suspicious activity. You need to develop and keep to best practices for your watch list. Investigate and drop users off the watch list quickly, and lean on your security analytics to keep tabs on the abnormal behaviour for you.
Take insider threats seriously, and most importantly, monitor your users and your data. Varonis gives you peace of mind that your data and your users are staying in their lanes. But if they aren’t you get a full context alert and associated logging to begin a thorough investigation.
Watch Troy Hunt’s video training series “The Enemy Within: Understanding Insider Threats” to learn more.
We’re Varonis. We’ve been keeping the world’s most valuable and vulnerable data safe since 2005. Our market-leading data security platform ensures that only the right people have access to data at all times, all use is monitored, and threats are flagged. Check it out or try it free.
For more information contact Grant Russell at [email protected] who is your locally based Scottish representative.