Zimbra Collaboration Suite Email Servers, versions older than Zimbra 8.8.15 patch 33 or Zimbra 9.0.0 patch 26.
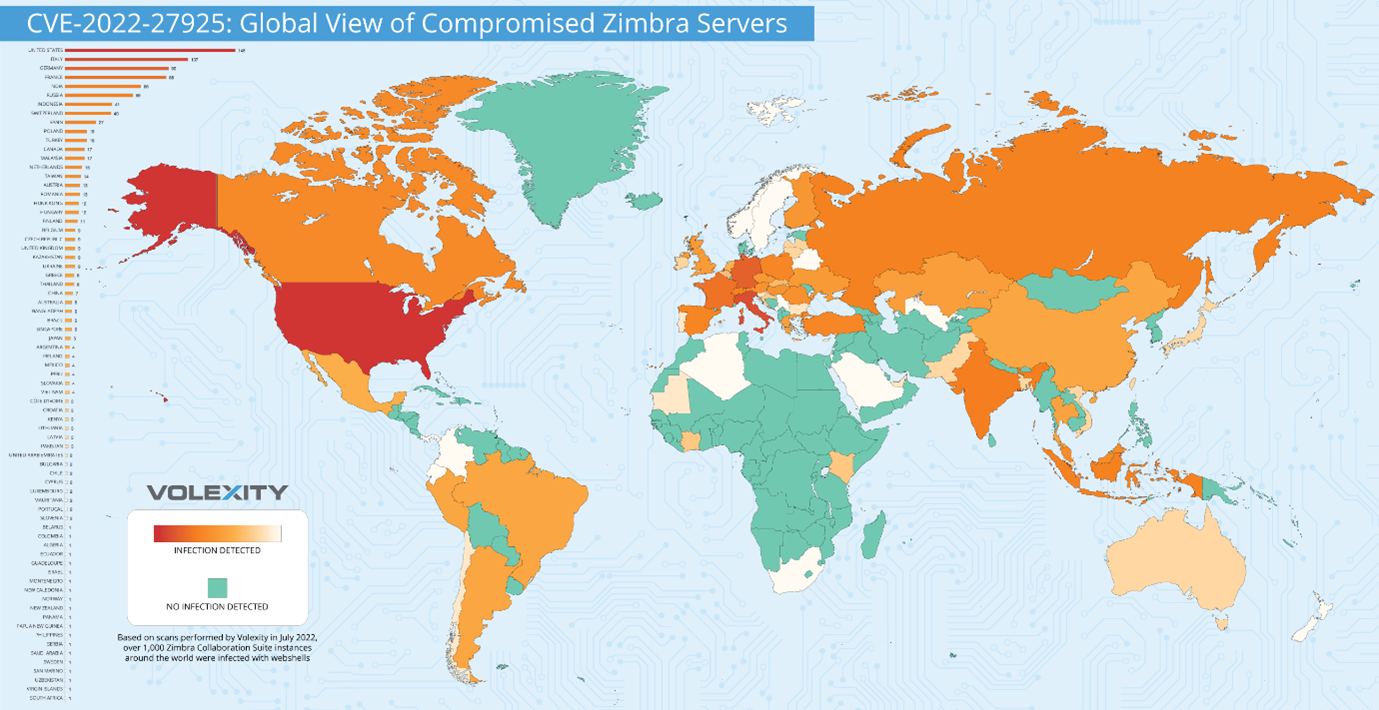
A currently unknown threat actor has been exploiting an authentication bypass vulnerability to access Zimbra Collaboration Suite (ZCS) email servers worldwide, according to the research team at threat intelligence firm Volexity.
Currently, over 1000 email servers scanned by Volexity have been confirmed to be compromised, however the true number may be much higher. These servers belong to a number of global organisations, and range from government departments and international businesses to small businesses which are “unlikely to have dedicated IT staff to manage their mail servers, and perhaps less likely to be able to effectively detect and remediate an incident” researchers stated.
Attackers have been targeting ZCS systems by exploiting a remote code execution bug tracked as CVE-2022-27925, alongside an authentication bypass bug tracked as CVE-2022-37042 – which was only patched on August 10th 2022.
Volexity’s full technical description of this attack can be read here. Zimbra has made a post detailing the patches for this threat, which can be found here.
Zimbra has strongly advised anyone running a Zimbra version that is older than Zimbra 8.8.15 patch 33 or Zimbra 9.0.0 patch 26 to immediately update to the latest patch.
Volexity has advised that anyone who did not apply patches 8.8.15P31 or 9.0.0P24 before the end of May 2022 may have a compromised email server, and so should preform a full analysis of the server to check for any malicious activity if possible. They have provided detailed steps on how to do this in their post on the subject, which can be found here.